CCleaner is a popular program for cleaning up computers. Amongst the host of similar programs out there, CCleaner is the only one I’ve used and trusted, for many years. This week, that trust has been undermined fundamentally.
A version of CCleaner was released during August that contained malicious code, presumably without the developers’ knowledge – though it could well have been an inside job. Anyone installing CCleaner during August/early September may have installed the compromised version of CCleaner – version 5.33.
This is serious. CCleaner is powerful software. The injected code would run with at least the same power of CCleaner, which means it could potentially:
- Watch your browsing activity
- Capture passwords
- Steal your files
- Compromise your online banking credentials
- Delete arbitrary data
- Encrypt files
And so on.
You can see if you’re at risk by running CCleaner and checking the version number:
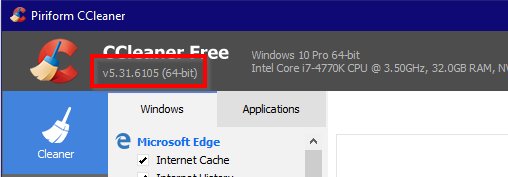
If you have version 5.33 version installed, I strongly recommend taking the following steps:
- Uninstall CCleaner immediately
- Change all passwords you use with the affected computer – including online passwords, banking passwords, etc.
- Review bank account and credit card statements for unusual activity
In many cases, you can add an extra layer of protection to your passwords by using “two factor authentication” (Google calls it 2-step verification). When logging into certain services, you will be prompted to enter a code from a text message or app. Even if your password has been compromised, two-factor authentication makes it that bit harder for others to gain access to your accounts.
For more information on two factor authentication (“2FA”):
CNET: Two factor authentication what you need to know
PCMag: Two factor authentication – who has it and how to set it up
For a list of services known to support 2FA:
Cisco’s security research team Talos advises that the ultimate target seems to be prominent tech companies. There’s evidence to suggest that a Chinese group has used this injected malware to launch further targeted attacks on companies like Sony, Intel, Samsung, Microsoft and several others. The most likely objective here is to steal intellectual property.
Should that make us any less concerned? Probably not. Such a serious compromise in a widespread, popular program undermines trust in software supply chains generally. There isn’t an awful lot we can do to defend against this sort of approach, other than to proceed with caution when installing any software. Best to stay away from the latest, bleeding-edge releases, perhaps.
Avast, the popular antivirus manufacturer owns CCleaner. If this can happen to a leading software security company, it can happen to anyone.
Run for the hills!!! 😀

