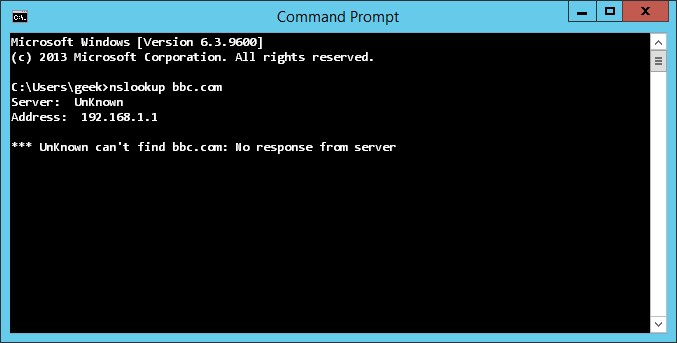
OCS Inventory NG forms an essential part of my DevOps/Security strategy. OCS gives me visibility of the hardware and software inventory of all compute nodes in my network.
My primary user directory is AD, so I try and ensure that wherever possible, systems authenticate against AD. This is perfect when disabling accounts, when someone leaves. Less worrying about all the other places that person may have credentials.
I’ve found that the instructions for authenticating OCS against LDAP simply don’t work for Active Directory. That’s up to and including the most recent version at the time of writing – version 2.4.
It’s necessary to make a code change, for AD authentication to work. In an ideal world, I’d raise a pull request with the OCS team to fix this, but I’m not really a developer. I’ve chosen instead the line of least resistance: hack the code to make it work. Sometimes you just have to be pragmatic.
The fix isn’t documented as far as I can tell. I’m indebted to Bruno Lessa for discovering and/or writing up the code changes that are necessary to enable authentication with Active Directory.
So, here are the code changes you need to make, after installing OCS Inventory. Some of the files may be in a slightly different location, in your installation, depending on your operating system. My installation was on Ubuntu 16.04 – I imagine the location is pretty similar on other OSes too.
| File | Find line containing | Change to |
|---|---|---|
| /usr/share/ocsinventory-reports/ocsreports/backend/AUTH/auth.php | $list_methode = array(0 => “local.php”); | $list_methode = array(0 => “ldap.php”, 1 => “local.php”); |
| /usr/share/ocsinventory-reports/ocsreports/backend/identity/identity.php | $list_methode = array(0 => “local.php”); | $list_methode = array(0 => “ldap.php”, 1 => “local.php”);? |
Having made those code changes, you configure LDAP in the web interface (Config > Config > LDAP configuration). Values similar to those below:
| Setting | Example value |
|---|---|
| CONEX_LDAP_SERVEUR | PROD-DOMC-01.mydomain.com |
| CONEX_ROOT | CN=ldapreadonlyuser,OU=Accounts,DC=yourdomain,DC=com |
| CONEX_ROOT_PW | ldapreadonlypassword |
| CONEX_LDAP_PORT | 389 |
| CONEX_DN_BASE_LDAP | OU=Accounts,DC=yourdomain,DC=com |
| CONEX_LOGIN_FIELD | samaccountname |
| CONEX_LDAP_PROTOCOL_VERSION | 3 |
| CONEX_LDAP_CHECK_FIELD1_NAME | memberof |
| CONEX_LDAP_CHECK_FIELD1_VALUE | CN=SysOps Admins,OU=SysOps,OU=Groups,DC=yourdomain,DC=com |
| CONEX_LDAP_CHECK_FIELD1_ROLE | Super administrators |
| CONEX_LDAP_CHECK_FIELD2_NAME | memberof |
| CONEX_LDAP_CHECK_FIELD2_VALUE | CN=SysOps Operators,OU=SysOps,OU=Groups,DC=yourdomain,DC=com |
| CONEX_LDAP_CHECK_FIELD2_ROLE | RO |
| CONEX_LDAP_CHECK_DEFAULT_ROLE | [blank] |