 I’m storing this as an aide memoire, really, but it may help you too.
I’m storing this as an aide memoire, really, but it may help you too.
Let’s say we have two systems, System_From and System_To. And two users, User_From and User_To. The objective is: log on to System_To as User_To, from System_From as User_From.
The steps
1. One-time key generation for User_From
On System_From, while logged on as User_From, proceed as follows:
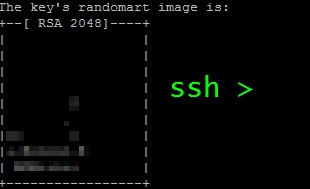
User_From@System_From:~$ ssh-keygen Generating public/private rsa key pair. Enter file in which to save the key (/home/User_From/.ssh/id_rsa):[hit enter] Enter passphrase (empty for no passphrase):[hit enter] Enter same passphrase again:[hit enter] Your identification has been saved in /home/User_From/.ssh/id_rsa. Your public key has been saved in /home/User_From/.ssh/id_rsa.pub. The key fingerprint is: be:e8:98:4a:26:1e:9b:ed:78:a7:e7:fe:d8:9d:3c:6d User_From@System_From The key's randomart image is: +--[ RSA 2048]----+ | | | E | | | | Q | | S | | . | |oo o o | |+.Bo8ooo.E | | BOB++o++ | +-----------------+
Note: if you use anything other than an empty passphrase, you will need to enter the passphrase each time you log on, which sort of defeats the object of this exercise!
This creates two files: id_rsa and id_rsa.pub. The private key, id_rsa, must always be kept secret. Your system should have marked it read/write for the owner only. The public key, id_rsa.pub is safe to copy to destination systems (see next section).
2. Copy the public key to System_To
OpenSSH comes with a handy script for copying the public key to the remote host (System_To, in this instance): ssh-copy-id. Use it like this, at the system you’re connecting from:
User_From@System_from:~$ ssh-copy-id -i ~/.ssh/id_rsa.pub User_To@System_To User_To@System_To's password:[type User_To's password and hit enter] Now try logging into the machine, with "ssh 'User_To@System_To'", and check in: ~/.ssh/authorized_keys to make sure we haven't added extra keys that you weren't expecting.
If you’re connecting to SSH on a custom port, the command is thus:
ssh-copy-id -i ~/.ssh/id_rsa.pub "User_To@System_To -p custom#"
Repeat this step for all remote hosts to which you intend to connect.
3. Log in to System_To
Now, when you issue the command ssh System_To, you will be logged in straight away, with no password prompt.